Author
Published
3 Feb 2025Form Number
LP2142PDF size
16 pages, 2.6 MBAbstract
A Kernel Live Dump is a snapshot of the Windows operation system’s kernel state taken while the system is running, without causing a crash or requiring a reboot. This feature is primarily used for diagnosing and troubleshooting abnormal behaviors where a crash has not occurred.
This paper introduces the background of kernel live dump and explains how to manually generate a kernel live dump by using a PowerShell cmdlet and Task Manager.
Introduction
A kernel live dump is a mechanism for capturing a snapshot of the system's memory without causing a crash or resetting the operating system.
A kernel live dump is non-disruptive so its primary benefit is to minimized downtime. Traditional crash dumps that are generated when the system crashes reset the operating system and disrupt user work, however, kernel live dumps allow the OS to continue to run while capturing memory information, which reduces downtime and user impact.
A Kernel live dump is effective for non-fatal issues. It is helpful in those scenarios where a crash has not occurred, but there are symptoms such as high CPU usage, memory leaks, or other abnormal behaviors.
Kernel Live dumps are similar to regular crash dump files, they can capture a consistent snapshot of kernel memory, including various memory pages including the following:
- KdDebuggerBlock
- Loaded Module List
- KiProcessorBlock
- PRCBs
- Current stack
- Current page directory table
- KI_USER_SHARED_DATA
- NTOS Kernel Image
- HAL Image
In this paper, we focus on kernel live dumps, which are code 0x161.These can be initiated manually by an administrator using Task Manager or a PowerShell command line.
Experiment: Using WinDbg to display the kernel live dump stop code information if created by Task Manager and PowerShell
0x161 is a stop code for kernel live dumps, it indicates the system administrator requested the collection of a kernel live dump. This code is used to identify live dumps only and never be used for a real bug check.
If the live dump is created by Task Manager, you can see the 1st parameter is 0x005461736b6d6772, it means this file is created by Task Manager since this value is a hexadecimal encoding for the text string ‘Taskmgr’.
0: kd> .bugcheck
Bugcheck code 00000161
Arguments 00546173`6b6d6772 00000000`00000000 00000000`00000000 00000000`00000000
0: kd> k
# Child-SP RetAddr Call Site
00 fffffc05`f6f5a310 fffff801`781565d5 nt!IopLiveDumpCollectPages+0xd9
01 fffffc05`f6f5a360 fffff801`78725307 nt!IopLiveDumpEndMirroringCallback+0x55
02 fffffc05`f6f5a390 fffff801`78155bfa nt!MmDuplicateMemory+0x2e7
03 fffffc05`f6f5a420 fffff801`78155cdc nt!IopLiveDumpCapture+0x86
04 fffffc05`f6f5a480 fffff801`780a9fca nt!IopLiveDumpCaptureMemoryPages+0x50
05 fffffc05`f6f5a5c0 fffff801`7813aa4e nt!IoCaptureLiveDump+0x432
06 fffffc05`f6f5a7f0 fffff801`786f1caf nt!DbgkCaptureLiveKernelDump+0x336
07 fffffc05`f6f5a890 fffff801`7828a255 nt!NtSystemDebugControl+0xc41bf
08 fffffc05`f6f5a9b0 00007ffc`d2563054 nt!KiSystemServiceCopyEnd+0x25
09 0000007b`b6f7f838 00000000`00000000 0x00007ffc`d2563054
0: kd> .formats 00546173`6b6d6772
Evaluate expression:
Hex: 00546173`6b6d6772
Chars: .Taskmgr
If the live dump is created by PowerShell, you can see the same stop code but the 1st parameter is null.
0: kd> .bugcheck
Bugcheck code 00000161
Arguments 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000
0: kd> k
# Child-SP RetAddr Call Site
00 ffffbd09`a52ced50 fffff802`d57565d5 nt!IopLiveDumpCollectPages+0xd9
01 ffffbd09`a52ceda0 fffff802`d5d25307 nt!IopLiveDumpEndMirroringCallback+0x55
02 ffffbd09`a52cedd0 fffff802`d5755bfa nt!MmDuplicateMemory+0x2e7
03 ffffbd09`a52cee60 fffff802`d5755cdc nt!IopLiveDumpCapture+0x86
04 ffffbd09`a52ceec0 fffff802`d56a9fca nt!IopLiveDumpCaptureMemoryPages+0x50
05 ffffbd09`a52cf000 fffff802`d573aa4e nt!IoCaptureLiveDump+0x432
06 ffffbd09`a52cf230 fffff802`d5cf1caf nt!DbgkCaptureLiveKernelDump+0x336
07 ffffbd09`a52cf2d0 fffff802`d588a255 nt!NtSystemDebugControl+0xc41bf
08 ffffbd09`a52cf3f0 00007ffc`c6dc3054 nt!KiSystemServiceCopyEnd+0x25
09 000000bb`ce27d458 00007ffc`9077eddf ntdll!NtSystemDebugControl+0x14
0a 000000bb`ce27d460 00000000`00000000 mispace!CLogCollectionServer::CaptureLiveDump+0x1b3
Using Task Manager to trigger a Kernel Live Dump
The Task Manager live dump feature is supported starting with Windows Server 2025.
To generate a kernel live dump using Task Manager, follow these steps:
- Search “Task Manager” to start Windows Task Manager.
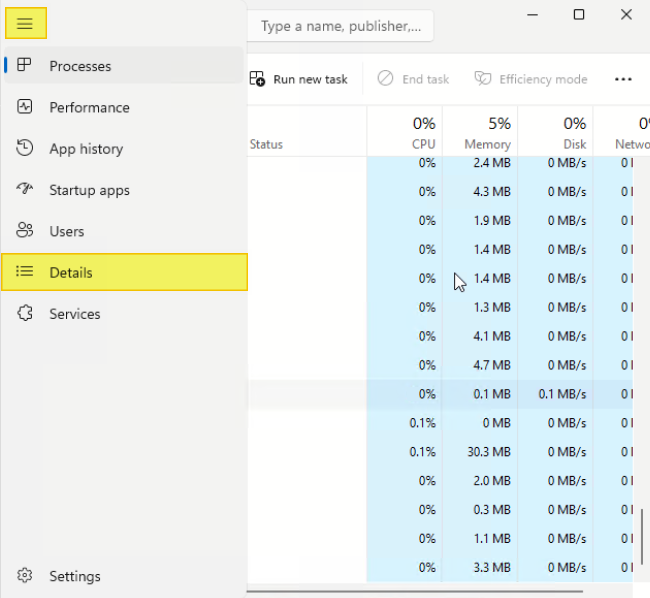
- Click the top left “Navigate” to Details.
- Find the System.
- Right click and select Create live kernel memory dump file. Then, select either a Full live kernel memory dump or a Kernel stacks memory dump from the pull-down menu.
The main differences between these two choices are as follows:
- Full live kernel memory dump:
- Contains active kernel memory.
- Optional inclusion of hypervisor of hypervisor memory and user-mode memory.
- Completed snapshot of the system’s kernel memory.
- Kernel stacks memory dump:
- The file size is smaller than the full live kernel memory dump.
- Limited to kernel processor stats and all kernel thread stacks.

Figure 4. Create live kernel memory dump file by Task Manager - Full live kernel memory dump:
- The kernel live dump will be created when the collecting is complete. The file is located at the default path:
C:\Users\<YourUserName>\AppData\Local\Microsoft\Windows\TaskManager\LiveKernelDumps
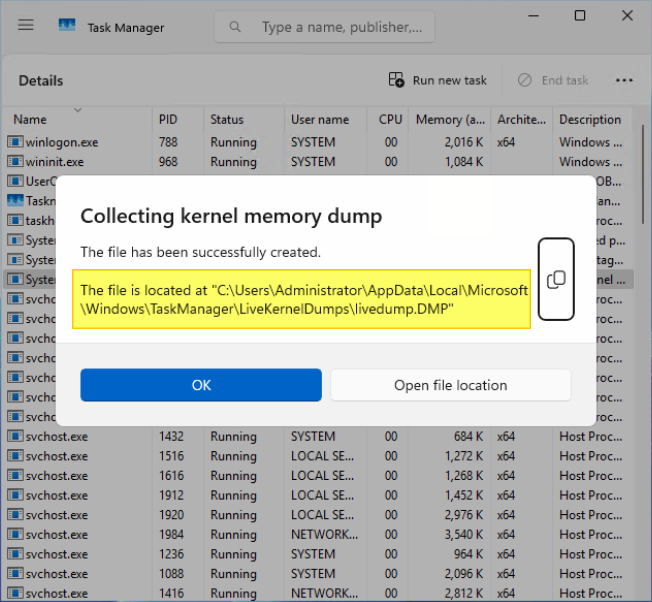
Figure 5. The kernel live dump is created at the default path
Using PowerShell to trigger a Kernel Live Dump
To generate a kernel live dump using PowerShell, follow these steps:
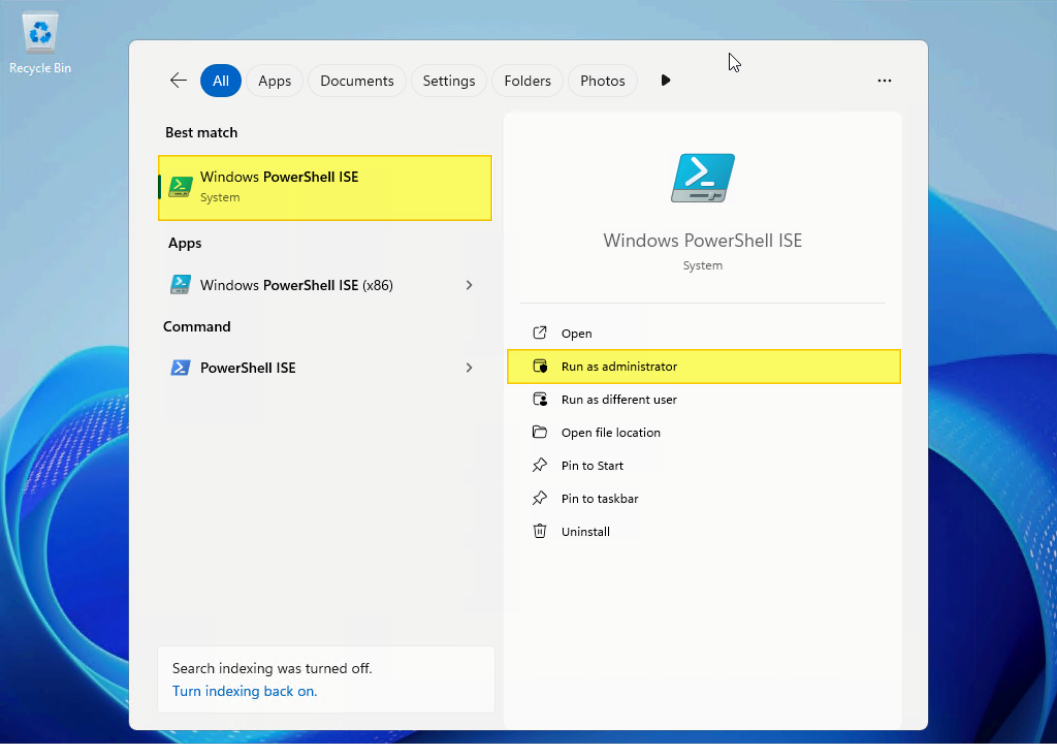
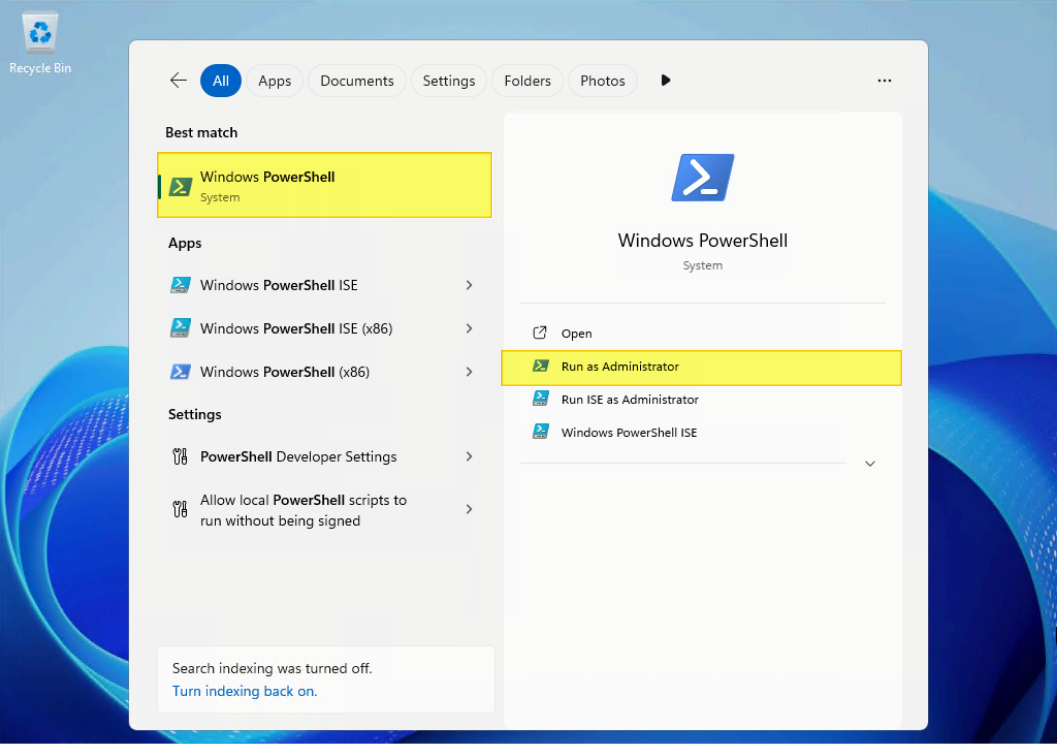
- Search “Windows PowerShell Integrated Scripting Environment (ISE)” and select “Run as administrator”.
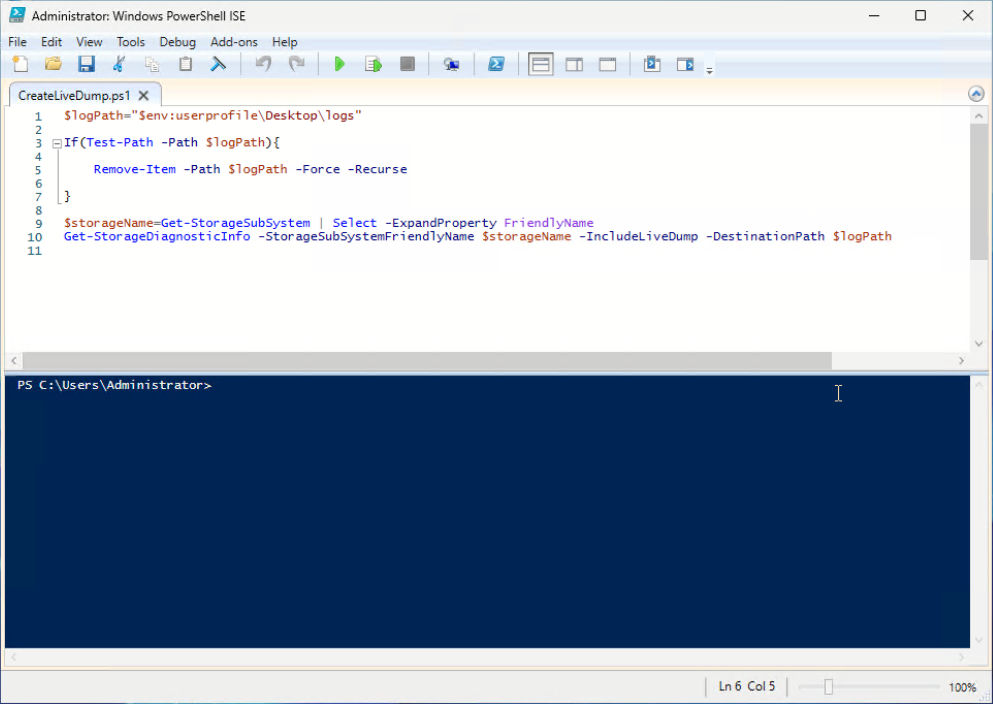
- Copy and paste the following code to PowerShell ISE to create a PowerShell script. For example, save it as a file named CreateLiveDump.ps1.
Set-ExecutionPolicy -ExecutionPolicy Bypass -Scope Process $logPath="$env:userprofile\Desktop\logs" If(Test-Path -Path $logPath){ Remove-Item -Path $logPath -Force -Recurse } $storageName = Get-StorageSubSystem | Select-Object -ExpandProperty FriendlyName Get-StorageDiagnosticInfo -StorageSubSystemFriendlyName $storageName -IncludeLiveDump -DestinationPath $logPath - Launch PowerShell as administrator. Search “Windows PowerShell” and select “Run as Administrator”.
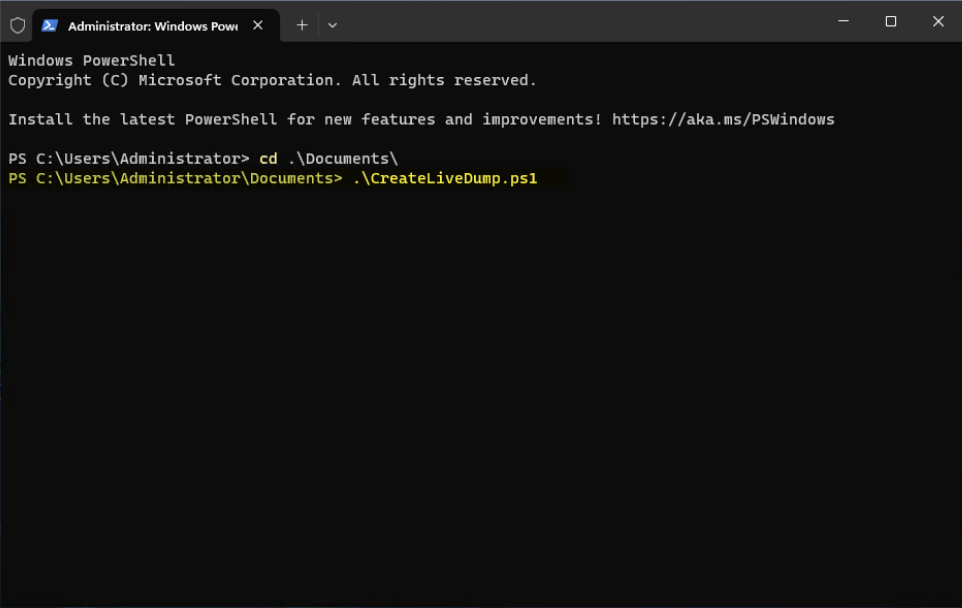
- Run the PowerShell script created in step 2.
- After running the script, the system starts to gather a kernel live dump in the specified storage subsystem.
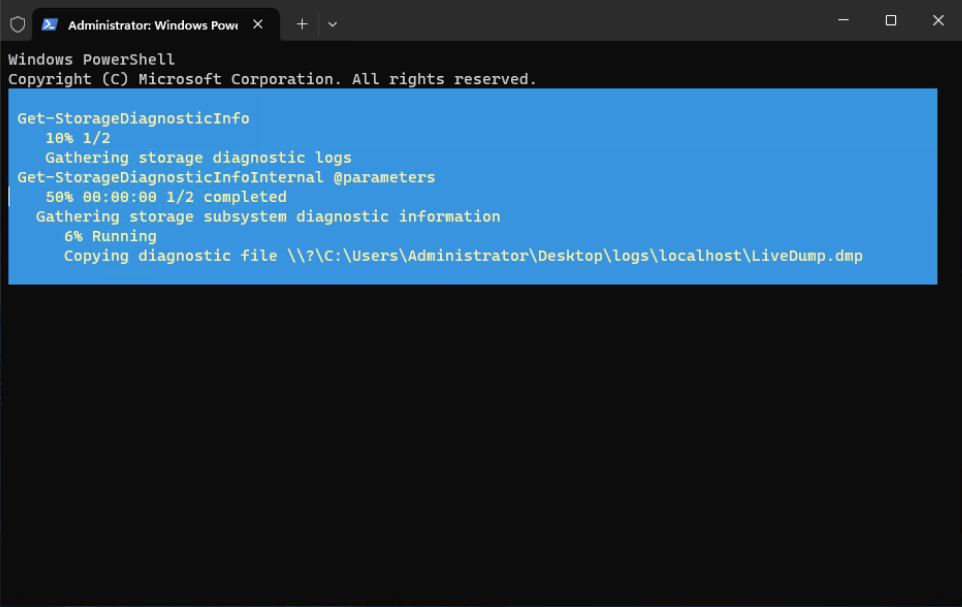
Figure 10. Gather the storage diagnostic informationNote: In this paper, we focus on how to manually trigger a kernel live dump on the system, so this using a PowerShell script to help to gather information about the boot device. This type of live dump, similar to a full live kernel memory dump, can also be created by Task Manager.
- The folder “logs” is shown on the Desktop after finishing the progress. You can get the live dump under this folder.
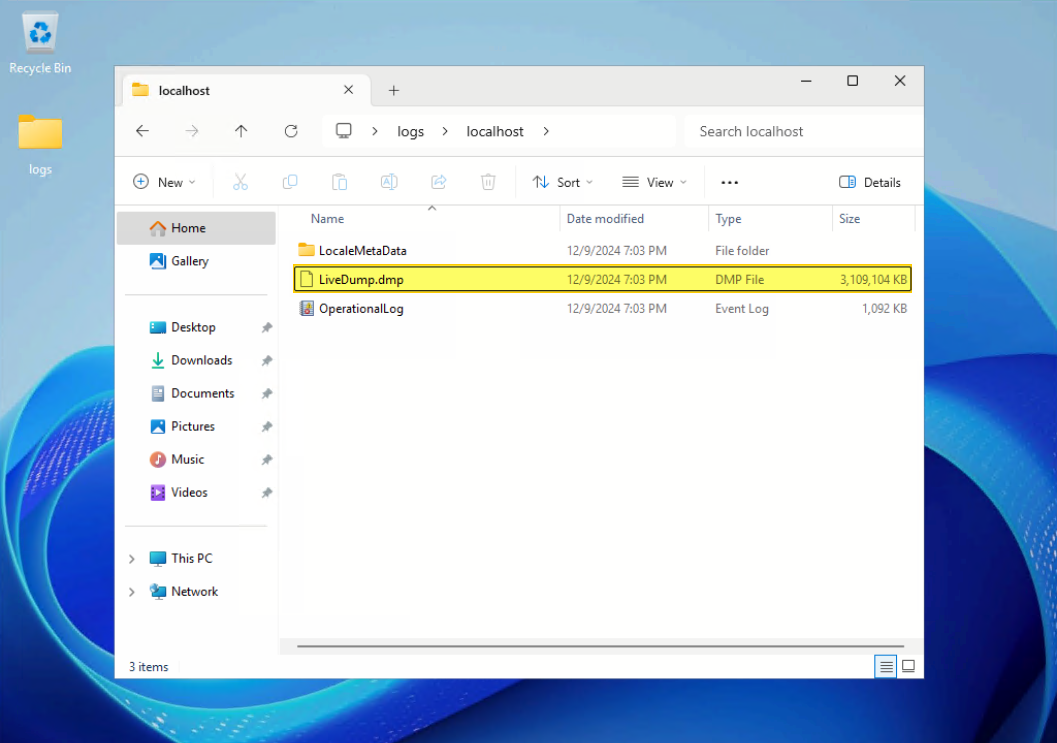
Figure 11. The kernel live dump is created on the folder logs
References
For more information, see these resources:
- Microsoft Learn, “Kernel Live Dump Code Reference,”
https://learn.microsoft.com/en-us/windows-hardware/drivers/debugger/kernel-live-dump-code-reference - Microsoft Learn, “Task Manager live memory dump,”
https://learn.microsoft.com/en-us/windows-hardware/drivers/debugger/task-manager-live-dump - Microsoft Learn, “Bug Check 0x161: LIVE_SYSTEM_DUMP,”
https://learn.microsoft.com/en-us/windows-hardware/drivers/debugger/bug-check-0x161--live-system-dump - Microsoft Learn, “Get-StorageDiagnosticInfo,”
https://learn.microsoft.com/en-us/powershell/module/storage/get-storagediagnosticinfo?view=windowsserver2025-ps
Author
Wewe Chang is a Windows Engineer in the Lenovo Infrastructure Solutions Group, based in Taipei, Taiwan. She has more than 10 years of experience with Windows kernel and user mode debugging.
Special thanks to the following people for their contributions and suggestions:
- Boyong Li, Senior Engineer, OS Enablement
- Ronald Arndt Jr, Advisory Engineer, ThinkAgile Development
- Gary Cudak, OS Architect, ThinkAgile Development
- Jieting Li, Information Development
- David Watts, Lenovo Press
Trademarks
Lenovo and the Lenovo logo are trademarks or registered trademarks of Lenovo in the United States, other countries, or both. A current list of Lenovo trademarks is available on the Web at https://www.lenovo.com/us/en/legal/copytrade/.
The following terms are trademarks of Lenovo in the United States, other countries, or both:
Lenovo®
ThinkAgile®
The following terms are trademarks of other companies:
ISE™ is a trademark of Advanced Micro Devices, Inc.
Microsoft®, PowerShell, Windows PowerShell®, Windows Server®, and Windows® are trademarks of Microsoft Corporation in the United States, other countries, or both.
Other company, product, or service names may be trademarks or service marks of others.
Configure and Buy
Full Change History
Course Detail
Employees Only Content
The content in this document with a is only visible to employees who are logged in. Logon using your Lenovo ITcode and password via Lenovo single-signon (SSO).
The author of the document has determined that this content is classified as Lenovo Internal and should not be normally be made available to people who are not employees or contractors. This includes partners, customers, and competitors. The reasons may vary and you should reach out to the authors of the document for clarification, if needed. Be cautious about sharing this content with others as it may contain sensitive information.
Any visitor to the Lenovo Press web site who is not logged on will not be able to see this employee-only content. This content is excluded from search engine indexes and will not appear in any search results.
For all users, including logged-in employees, this employee-only content does not appear in the PDF version of this document.
This functionality is cookie based. The web site will normally remember your login state between browser sessions, however, if you clear cookies at the end of a session or work in an Incognito/Private browser window, then you will need to log in each time.
If you have any questions about this feature of the Lenovo Press web, please email David Watts at dwatts@lenovo.com.